Wigle.net is a crowd sourced collection of wireless network information produced through war driving activities. Viewing search results requires registration but there is no subscription fee for the service. The site uses the Google Maps API and GPS data captured during war driving activities to identify the presence of wireless network observations within range of a given search location.
The following is typical methodology for performing reconnaissance using wigle.net:
- Enter the physical address of the target facility in the wigle.net search field and click the magnifying glass icon.
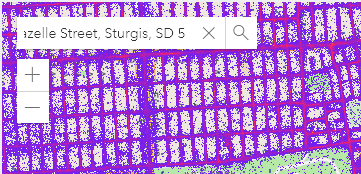
- Use the zoom feature to narrow results down to the target facility. When you zoom in sufficiently, SSID values will appear in the map.
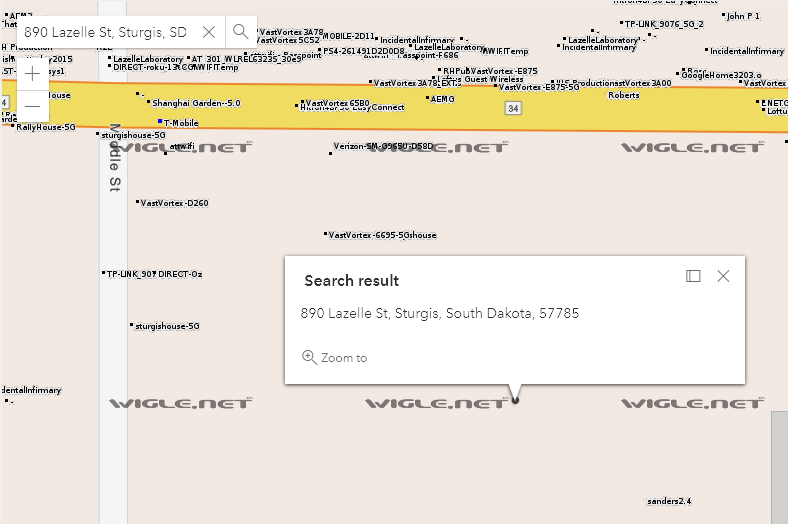
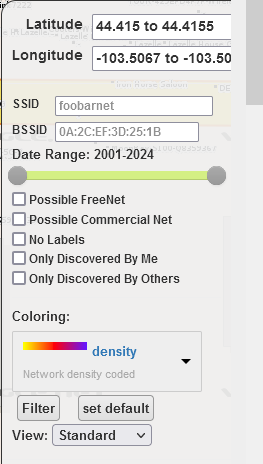
- Visually search the results for networks that may be attributed to the target organization. This can be accomplished through simple observation (organic discovery) or using the SSID list provided by the customer. Filtering can be applied to narrow search results. The filter bar includes controls to filter on SSID, BSSID, and narrow the observation time.
- After discovering a network instance, click on one of the instances in the map. This will cause details about the network to be displayed in the map, including the SSID, BSSID, observation details, channel, and encryption details.
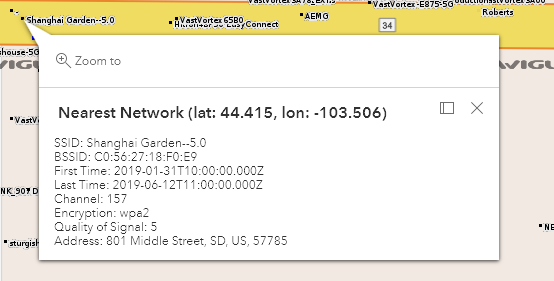
- Copy the BSSID value from the displayed result, paste the value into the BSSID field of the filter bar, remove the last byte of the MAC address, and click the filter button.
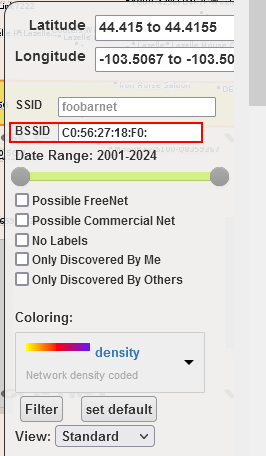
This filter criteria will display all SSIDs that share the same base BSSID, indicating that they are potentially hosted on the same hardware. When access points are used to host multiple SSIDs, the device will often use a MAC address that is incremented using some pattern. Frequently, the last byte of the MAC address is the value that gets incremented when the new SSID is provisioned. As a result, doing basic MAC analysis may allow you to discover additional SSIDs associated with customer equipment.
Similar analysis should be performed while onsite using Kismet, Netspot, or other network discovery tools.